Pentagon twitter hack: ‘What the command is doing there?’
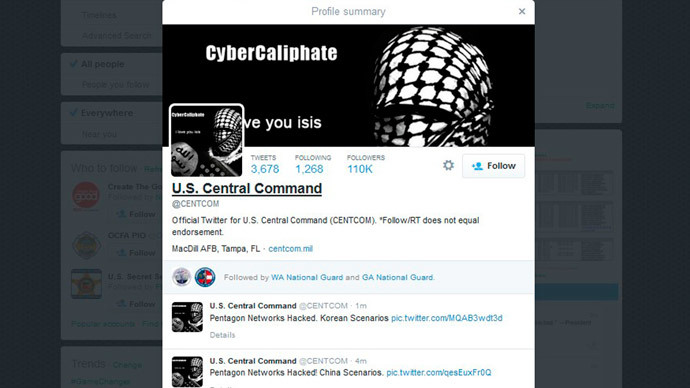
The hack of the US Central Command Twitter account raises questions over what the command is doing: it is supposed to be a war fighting machine rather than engage in public diplomacy, Larry Johnson, retired CIA and State department official, told RT.
RT:The cyber vulnerability of the US government has been exposed in an official probe. How's it even possible that the country which has been spying on its own people and the whole world, doesn't even have a strategy to defend against hackers?
Larry Johnson: Collecting information is far different from being able to create safeguards from people intruding on that... [The US] is like a vacuum cleaner, it can sweep up a lot of information but being able to sweep up that information doesn’t mean it is able to process it and use it in an effective manner. In tandem with that we’ve seen is that the systems are fragmented across the US government. Some might consider that a good security measure... But what happened the other day at Central Command, the fact that they have a public twitter account raises questions about: “What are they doing?” This is a military command. They are not out there supposed to be engaged with public diplomacy, they are supposed to be a war fighting machine. And I can understand having a public portal for some limited activities. But still you should take measures to protect that against this kind of hacking activity, and clearly they were unprepared to do it. It is a sort of an expression in English “being a redheaded stepchild,” the person who doesn’t really remember the family that gets the top priority gets left behind…
READ MORE:Central Command Twitter account apparently hacked by CyberCaliphate
RT:What about the hacking of the YouTube and Twitter accounts used by the US military's Central Command? Were they too unprotected, or was there another reason why this was possible in the first place?
LJ: It is not a classified system and they probably decided not to spend many resources on it. But by virtue of doing that they only are making it very right fat target.
The Department of State has lots of publically available websites. You get across the board in the US government every different department and agency has a website of some sort. Yet, when you really get into it those, you can quickly discover that there is no common practice or procedure or uniform system of, let’s call it, security compliance. There is no general standard that is in force to apply across the board to make sure that everybody is doing everything in the same way in order to make it difficult for hackers to attack. Instead some do it better than others and there are great gaping vulnerabilities across the spectrum.
RT:Last year we also saw the hacking of Sony Pictures, which the US government blamed on North Korea. Why is America increasingly becoming a target for hackers?
LJ: It is probably more a perception but it is simply a function and the fact that people are becoming more and more computer dependent. You think back what was like 20 years ago with the number of people being on cell phones, on computers, and social media being virtually non-existent back then. So we’ve seen a genuine revolution and it is accelerating to the point that it’s creating a global phenomenon in which we are able to integrate…
The statements, views and opinions expressed in this column are solely those of the author and do not necessarily represent those of RT.
The statements, views and opinions expressed in this column are solely those of the author and do not necessarily represent those of RT.












