‘NotPetya’ hackers demand $260,000 in first communication since attack
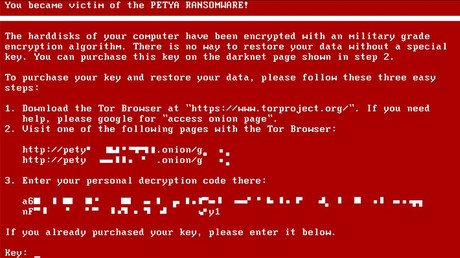
The alleged hackers behind a ransomware attack that crippled computer systems across the globe last month have surfaced online, demanding over $260,000 in exchange for a private key that they claim can decrypt any data affected by the attack.
The post appeared on the Tor-only announcement service DeepPaste, demanding 100 bitcoins (roughly $262,000). It’s the first statement since last month’s attack and contained a file signed with their private key, described by Motherboard as “strong evidence” that it came from those responsible.
Hackers connected to #NotPetya ransomware surface online and empty bitcoin wallet https://t.co/tzcr3VqrBqpic.twitter.com/bkFipkX3e9
— Lorenzo Franceschi-B (@lorenzoFB) July 5, 2017
The ransomware used in the attack was a variant of a virus known as Petya, earning the group the name, ‘NotPetya.’
New: hackers linked to #NotPetya decrypted a file provided by Motherboard. Complicates the already bizarre story https://t.co/YcUCkllsDnpic.twitter.com/ytrs6u7d2J
— Joseph Cox (@josephfcox) July 5, 2017
No bitcoin wallet address was included in the message, instead, a link to a chat room where they could be contacted. In the chat room, Motherboard were told by someone claiming to be one of the hackers, that the price was high because it was the key “to decrypt all computers.”
The statement came shortly before a bitcoin address used in the ransomware attack was debited with $10,000 in payouts. The account, which had been accumulating bitcoins from those who agreed to pay the ransom, was left almost empty following the withdrawal.
Apart from making the announcement on Pastebin and DeepPaste, sites used by hackers for communicating, the suspects also provided proof that they were the real perpetrators. Forbes checked a signature for the malware’s private key, provided by the alleged hackers, with two separate malware researchers who said it was real.
The ransomware attack reportedly began in Ukraine, but has since spread to corporate systems across the world, affecting the Russian state oil giant Rosneft, the international shipping and energy conglomerate Maersk, and the UK-based advertising and public relations company WPP, among others.
The Ukrainian interior minister said in a statement posted to Facebook that police had managed to stop a second stage of the attack, shutting down and confiscating computer servers believed to have aided the virus’ spread.
READ MORE: ‘State actor’ behind NotPetya cyberattack, expect ‘countermeasures’ – NATO experts
Kiev has also pointed the finger at Russia for the attack. NATO said it could “most likely be attributed to a state actor.”
The ransomware is similar in impact to “WannaCry,” a code derived from the US National Security Agency (NSA) and posted online by the hacker group ShadowBrokers. In May, a WannaCry ransomware attack shut down over 200,000 computers globally.