False flags & cyber wars: New Snowden leaks reveal Canada spy agency’s ‘deception toolbox’
Top secret documents from Edward Snowden’s cache have revealed Canada’s ambition to become a big player in the world of electronic spying. The leak comes just as the country plans to vote on a law that would give its cyber agencies more powers.
READ MORE: 'Freedom in jeopardy': Thousands rally across Canada against new anti-terror law
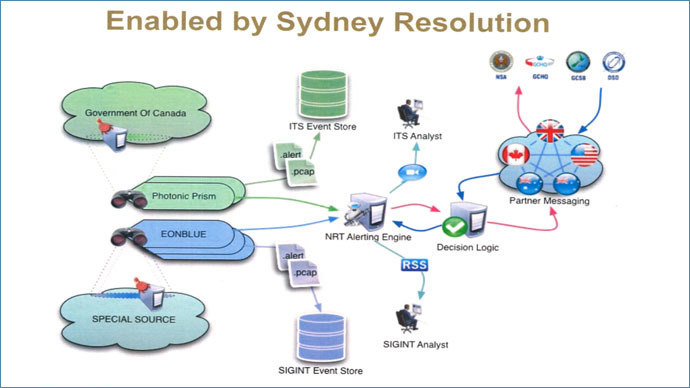
A confidential presentation by Canada’s intelligence agency Communications Security Establishment (CSE) dated 2011 was among the documents published jointly by the Canadian Broadcast Corporation and The Intercept, the website of investigative journalist Glenn Greenwald. In it, the counterpart of US National Security Agency (NSA) assures its Five Eyes allies – US, UK, Australia and New Zealand – that by 2015 it “will seek the authority to conduct a wide spectrum of Effects operations in support of our mandates.”

The C-51 bill, which would relax Canada’s stringent policing and intelligence regulations, is currently being pushed through parliament by the ruling Conservative party in the cause of combatting terrorism, but is facing spirited resistance, including filibusters from the opposition. Public demonstrations have also been staged against the legislation, which has been criticized as vague, shadowy and intrusive.
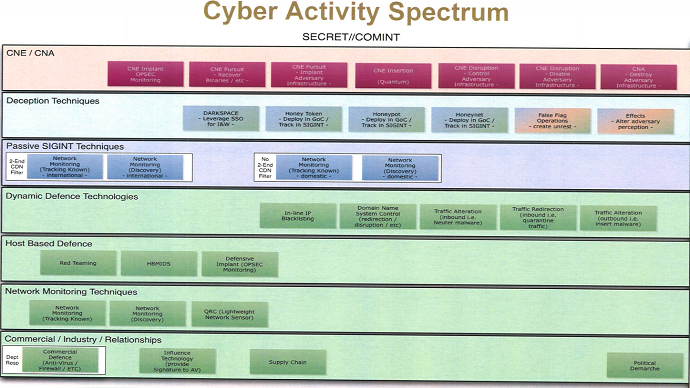
The allegedly leaked presentation shows 32 techniques that could be employed by the CSE – some defensive, others proactive. Among them are:
READ MORE: ‘When you collect everything, you understand nothing’ – Snowden
– ‘Computer network operations to destroy adversary infrastructure’: using electronic means to cause physical damage is an increasing priority. The most well-known example is Stuxnet, a likely US-Israeli virus that damaged Iran’s uranium enrichment centrifuges. But attack targets could include power stations, dams and airports. There are other options listed of controlling/disabling infrastructure;
– ‘False flag operations’: these create damage and then leave a trail of evidence that pins the blame on another country or agent;
– ‘Traffic Alteration’: intercepting enemy communications with the purpose of inserting malware, which can be used for inflicting damage.
While CSE said it was not at liberty to comment on the details,
it has published a series of written replies claiming the
documents are “dated” and “do not necessarily
reflect current CSE practices or programs.”
It has also simultaneously accused CBC and the Intercept of
“misunderstanding” the published files, and
“rendering our methods less effective.”
READ MORE: Anonymous hacktivist deported back to US after failed asylum bid
“In moving from ideas or concepts to planning and implementation, we examine proposals closely to ensure that they comply with the law and internal policies, and that they ultimately lead to effective and efficient ways to protect Canada and Canadians against threats,” CSE said in a statement.
Former NSA contractor and CIA employee Snowden distributed part of the classified documents exposing relentless mass surveillance by the US and its key allies to Canadian media. Previously leaked materials have already revealed that the CSE shares some of its tactics with the NSA and even allegedly uses the US agency’s cyber warfare software for some tasks.
READ MORE: Canadian faces $20k fine, jail time for refusing to unlock phone during airport check
Snowden’s leaks had shown that the CSE targets cellphones with the highly sophisticated WARRIORPRIDE malware and also maintains a botnet, or a whole network of infected private computers, to attack targets without giving itself away. Back in 2013, the NSA leaks implied that Canadians were also allegedly involved in spying on devices connected to the Brazilian mining and energy ministry – which was part of what prompted accusations of industrial espionage and a diplomatic row between Brasilia and Washington.












